Turn Compliance into Your Advantage
Meet regulatory demands confidently with CyberArk’s identity security platform, reducing complexity and ensuring resilience.

Audit & Compliance
Master Compliance with Confidence
Navigating the complexities of identity security, regulatory compliance, and audits doesn’t have to be a burden. With CyberArk, you can meet stringent regulatory requirements without compromising on efficiency or growth. Our unified platform ensures compliance is streamlined, secure, and stress-free, allowing you to focus on protecting your organization’s most valuable assets. Reduce audit costs, stay always prepared with real-time monitoring and reporting, and turn compliance into a powerful advantage that drives your business forward.
Cut Compliance Costs and Simplify Audits
CyberArk streamlines security audits, reducing time and costs tied to compliance. Focus on what truly matters: protecting your organization’s most critical assets and driving growth, all while ensuring you meet every regulatory requirement.
Always Be Ready for Your Next Audit
Stay audit-ready with CyberArk’s continuous monitoring, automated reporting, and real-time compliance management. Minimize surprises and maximize confidence, knowing your organization meets compliance standards with ease.
Leverage Compliance as a Strategic Asset
Transform compliance into a powerful enabler of innovation and growth. With CyberArk’s integrated identity security and compliance solutions, turn regulatory requirements into a competitive advantage for your business.
Achieve Continuous, Agile Compliance
Automate enforcement, remediate gaps, and reduce audit prep time with CyberArk’s compliance solutions.
Continuous Compliance, Automated Security
Ensure compliance with automated enforcement of access policies for a unified, strategic security approach.
Proactive Remediation for Compliance
Identify and resolve audit gaps early to stay ahead of regulations and avoid costly penalties.
Operational Agility in Audits
Cut audit prep time by 70% and focus on strategic goals while confidently meeting compliance requirements.
Unified Security for Total Compliance
Protect access, enforce least privilege, and integrate tools to streamline audits and strengthen security.
Secure privileged access
Compromised privileged identities are the leading cause of security breaches—which makes privileged access one of the biggest priorities for your business. The most secure privileged access approach prevents human and machine identities from having more access to systems and resources than they need.

Enforce least privilege
The least privilege principle ensures the right access is provided to the right users for the right amount of time. The practice extends beyond human access to include applications, systems or connected devices that require privileges or permissions to perform a required task.
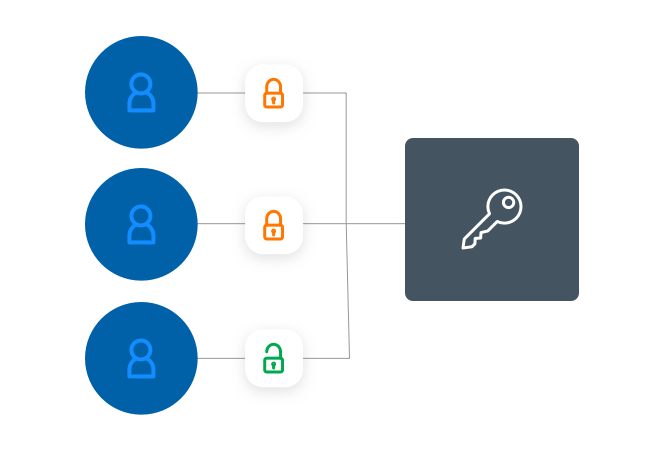
Enable strong authentication
Multi-Factor Authentication (MFA) and Single Sign-On (SSO) are two best practices for ensuring your users are who they claim to be. MFA secures your entire organization: Apps, VPNs, Workstations, etc. SSO provides secure and frictionless sign-in experience for both internal and external users.

Broker secure sessions
In a secure brokered session, privileged users are able to connect to systems without exposing credentials to end-users or their machines. The approach ensures accountability, identifies risk, and produces a tamper-proof audit trail.
Integrate with compliance tools
To address IT audit and compliance requirements, our Identity Security platform integrates with compliance and reporting tools. Consequently, you’ll be able to provide comprehensive and integrated reports on privileged access and session activities to address questions and pass an IT audit.

Proactive Compliance Programs

How to Build a Proactive Compliance Program with Identity Security
Streamline compliance initiatives, simplify audits and mitigate risk by implementing a comprehensive identity security strategy
Explore
related
resources
Request a demo
Improve confidence in achieving audit/compliance requirements
Reduce audit and compliance costs and time
Remediate audit gaps before they are flagged